Cybersecurity statistics reveal an intensifying battle against increasingly sophisticated threats, with profound implications for business leaders navigating digital transformation.
As attack surfaces expand and adversaries leverage emerging technologies, understanding these dynamics becomes critical for strategic risk management.
Below is an expanded analysis of 2025’s cybersecurity landscape, structured to inform decision-making across organizational hierarchies.
The economic impact and scale of cyber threats
Cyber attacks are a cost from multiple points of view.
Expenses destined to prevent and combat cybercrime are just the tip of the iceberg: the actual exposure or loss of data is a major factor that can destroy a business, especially if financial and sensitive data are exposed and the company involved becomes legally noncompliant.
Following up, we want to highlight some of the most relevant statistics that can drive cybersecurity-related decision making for the better.
- Global cybercrime costs reached $9.5 trillion in 2024, projected to hit $10.5 trillion by 2025 and $15.63 trillion by 2029 (surpassing the GDP of most nations).
As Statista mentions:
The global indicator ‘Estimated Cost of Cybercrime’ in the cybersecurity market was forecast to continuously increase between 2024 and 2029 by in total 6.4 trillion U.S. dollars (+69.41 percent). After the eleventh consecutive increasing year, the indicator is estimated to reach 15.63 trillion U.S. dollars and therefore a new peak in 2029. Notably, the indicator ‘Estimated Cost of Cybercrime’ of the cybersecurity market was continuously increasing over the past years.At the end of 2024, The Wall Street Journal indicates a staggering 750 million cyber attack attempts per day approximately (which translates to about 8,680 attacks per second, ed), a clear sign that hackers are leveraging AI for malicious purposes.

- The average data breach cost rose to $4.88 million in 2024, according to IBM, a 10% increase over last year and the highest total ever.
Industry-specific financial exposure
Quoting Grand View Research,
Large organizations invest heavily in AI-driven tools for threat detection, endpoint security, and risk management to address complex cybersecurity challenges.
In their assessment, the industries that are spending the most on AI-based security applications share the market as follows:
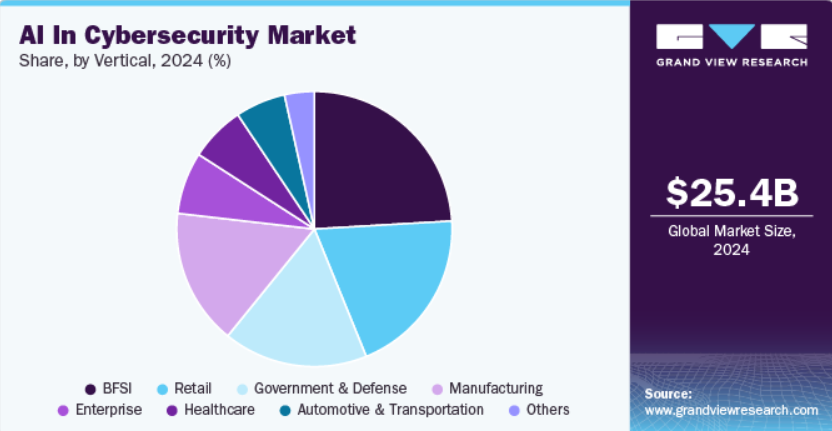
While the Finance sector is the most advanced in terms of security (World Economic Forum),
Furthermore:
- 55% of Healthcare organizations have planned to increase their cybersecurity investments across 2025.
- For the Energy sector, more than two-thirds (71%) of energy professionals expect their company to boost investment in cybersecurity within the year, reflecting a proactive approach to mitigating emerging threats.
Also, the same DNV research explains how 66% of energy professionals agree that attackers’ use of AI in phishing emails has made it more difficult to determine whether online messages are genuine.
Cybersecurity statistics: the evolution of attack methodologies
The last few years have seen a dramatic transformation in how cybercriminals operate.
What began as opportunistic malware or simple phishing scams has evolved into highly sophisticated, multi-vector attacks.
Fueled by automation, AI, and the proliferation of “as-a-service” cybercrime tools, modern attack methodologies are faster, more targeted, and harder to detect than ever before.
In fact, in 2025, attackers are increasingly adopting tactics once reserved for nation-states, from deepfake-powered social engineering to multi-stage supply chain infiltrations.
At the same time, the rise of cloud infrastructure, remote work, and interconnected platforms has expanded the attack surface dramatically, giving threat actors more ways in and defenders more ground to cover.
Here following, the most relevant statistics on this.
AI-driven threats
In the WEForum report Global Cybersecurity Outlook 2025, it’s noted that 66% of organizations look at AI as the biggest cybersecurity game-changer in 2025.
This is just one statistic that reflects the real deal in digital security: AI has changed the industry and requires everyone to adapt.
- According to the Cyber threat landscape report published by Viking in 2024, 53% of the companies feel unprepared for AI-powered attacks.
- Despite Generative AI being a game changer for organizations’ cybersecurity, some lack clarity on how to incorporate it in their business processes (39%, according to PwC).
Thus, AI is one key driver for advancements in security infrastructures.
During its 81st Annual General Meeting (AGM) on 10 November 2024, ICANN highlighted that generative AI makes it possible to randomize each specific domain or URL.
In practical terms, this allows cyber attackers to scale their operations by registering domains unpredictably, at random times and dates, and at scale, making threats harder to detect and block.
Cybersecurity statistics on ransomware 3.0
- As per a Sophos study, Double extortion tactics (data encryption plus leaks) now account for 76% of ransomware incidents, with average demands hitting $170,404 in 2023.
- Ransomware-as-a-Service (RaaS) groups are a threat to digital security. Yet, according to Chainanalysis, in 2024, ransomware attackers collected around $813.55 million in payments— a 35% drop from the record $1.25 billion in 2023— marking the first decline in ransomware revenues since 2022.
DNS abuse in 2025: the fundamental threats remain
Cybersecurity threats in 2025 are evolving fast, but some of the most dangerous threats remain deceptively simple. DNS abuse is one of them.
At its core, DNS abuse refers to the exploitation of the Domain Name System for malicious purposes (think phishing attacks, malware distribution, botnets, and spam).
But in today’s AI-driven landscape, it’s not just about bad actors hijacking domains: it’s about how they’re scaling their attacks.
According to ICANN’s enforcement update ICANN’s Enforcement of DNS Abuse Requirements – Six Months, 38% of all abuse-related investigations between April and October 2024 involved DNS abuse.
Although most of these were resolved at the informal stage, meaning they were real issues, caught early, and handled behind the scenes without escalating to a formal breach.
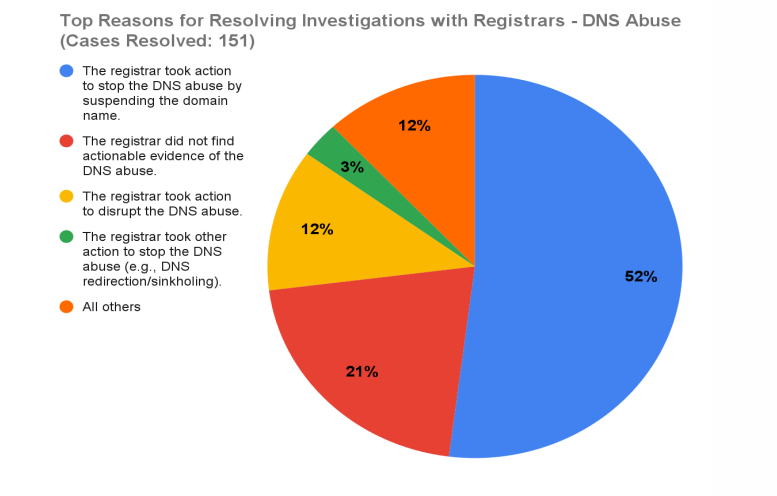
That’s a win for compliance, but also a reminder of just how frequently these threats occur.
Why it matters now
In 2025, cybercriminals are leveraging generative AI to create domain variants in real time, launching attacks through randomized domains at unpredictable intervals.
This makes traditional, reaction-based detection obsolete, as DNS abuse is no longer a static risk, but a dynamic, scalable, and automated practice.
And while many businesses focus on endpoint protection, email security, or firewall defenses, DNS often remains an overlooked weak point, despite being foundational to all online interactions.
Most common DNS-based exploit
As DNS activity remains a critical point to exploit for cyber attackers, domain name service requests meant to connect users to digital endpoints leave room for several types of threats.
CISCO has published a list of the most common attacks as investigated in their report Cyber Threat Trends Report: From Trojan Takeovers to Ransomware Roulette published; ordered by times they have spotted them, these are:
- Information stealers, which harvests private access and financial data
- Trojans, which are disguised malicious program
- Ransomwares, that encrypt data to blackmail users
- RAT (Remote Access Trojans), that give hackers remote control
- APT (Advanced Persistent Threat), or long-term and hidden intrusions
- Botnets, which are constituted by a network of infected computers
- Droppers, which install other malware on targeted systems
- Backdoors, which leave entry points for future attacks
Highlight: An unsafe website is worth nothing and endangers its users. Scan the security level of your website for free.
Organizational defense gaps in cybersecurity
Despite increased investment in cybersecurity, many organizations still fall short when it comes to closing critical defense gaps.
The complexity of modern IT environments (like hybrid infrastructures, SaaS sprawl, decentralized teams) has outpaced the security controls meant to protect them. And while threat actors move quickly and adapt with precision, internal defenses often lag behind, fragmented by silos, outdated tools, and lack of visibility.
In fact, setting up technical infrastructures capable of responding to advanced cybercrime is a primary concern, while specialized talent acquisition is another critical challenge.
We can look at these gaps from various points of view: talent shortage, vulnerabilities for small businesses and intrinsic risks of tech infrastructures.
Talent and resource shortfalls
- As per the World Economic Forum, 66% of organizations face moderate-to-critical cyber talent shortages, exacerbated by an 8% skills gap increase in 2024.
- The same WE Forum, had previously published a research where only 4% of enterprises declared to feel confident in IoT security capabilities (State of the Connected World, 2023 Edition)
While human talent is what organizations lack of, it’s also still the main cause of errors (74% of all data breaches is caused by it, according to Verizon’s 2025 Data Breach Investigations Report)
SMB vulnerabilities
- According to AAG IT report in 2025, 78% of small and medium businesses stated that they will increase investment in cybersecurity in the next 12 months
- Companies with 500–1,000 employees saw 21.4% higher breach costs in 2023 (The SSL Store), and Verizon had earlier reported that 46% of all cyber breaches impact businesses with fewer than 1,000 employees.
Geographical cybersecurity statistics and cyber-resilience
The cybersecurity market is one that shouldn’t grow: in an ideal digital and geo-political ecosystem, tech infrastructures are protected and used appropriately.
But, as it’s projected to grow to $298.5 billion by 2028, we feel that it is important to investigate how different territories project their capabilities of resilience towards their native organizations.
Geopolitical and regulatory complexities
When it comes to cybersecurity, both the private and public sector have an ingrained tie with the country they are set in and depend on.
When interviewed by the WEForum, companies have stated their opinion about the level of cyber-resilience of their country:
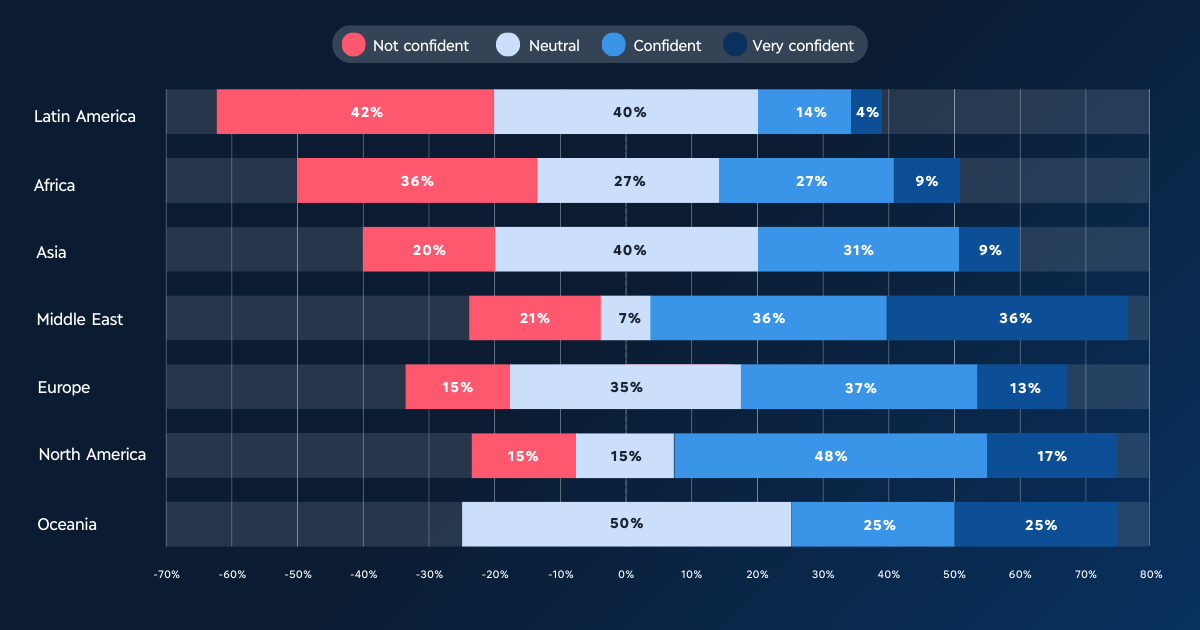
Outlook 2025, WEF
With the public sector notoriously generating less confidence than the private one.
When thinking of geo-political-based cyber attacks, it’s a common mistake to feel the reported disruption events or threats as distant; yet, a successful attack makes a proven case, which both serves as an example for hackers and as spotted vulnerability for companies to act on.
Furthermore:
- The conflict between Russia and Ukraine has endangered the global digital ecosystem, as cyber arms were one way to carry on the war.
To quote The Wire in this article dated February 2025:
Over the last decade, the Kremlin’s most aggressive cyberwar unit, known as Sandworm, has focused its hacking campaigns on tormenting Ukraine […] Now Microsoft is warning that a team within that notorious hacking group has shifted its targeting, indiscriminately working to breach networks worldwide—and, in the last year, has seemed to show a particular interest in networks in English-speaking Western countries.
- 76% of CISOs struggle with fragmented regulations across jurisdictions (World Economic Forum).
- Other past nation-state attacks have seen worrying incidents, like the one targeting US diplomatic communications in 2023.
Strategic recommendations for business leaders
Following up, we formulated a series of advices starting from key findings of the previous cybersecurity statistics.
- AI Integration with governance, which requires the deployment of generative AI for threat simulation, with implementation of pre-deployment security assessments.
- Supply chain audits, by mapping out third-party dependencies and mandate SOC 2 compliance for vendors, which is a major barrier for 54% of large enterprises’ cyber resilience (WEForum).
- Talent pipeline development, by investing in AI-driven training platforms shown to reduce employee-caused incidents by 40% by 2026 (Gartner), also acting on that 40% of cyber team members who intentionally don’t report cyber incidents out of fear of losing their jobs.
- Geopolitical contingency planning, by aligning threat intelligence with geopolitical risk teams to mitigate state-sponsored IP theft and disruption campaigns.
Cybersecurity statistics: conclusions
These cybersecurity statistics for 2025 paint a landscape where technological innovation outpaces defensive maturation.
While AI and zero-trust frameworks offer promise, systemic vulnerabilities in supply chains, talent pipelines, and geopolitical risk management persist.
The projected $10.5 trillion cybercrime toll (Virtasant, March 2025) underscores an urgent need for C-suites to transition from reactive compliance to anticipatory resilience architectures.
Organizations adopting integrated AI-human defense models, coupled with cross-sector threat intelligence sharing, will be best positioned to navigate this escalating crisis.
If you’re in the domain industry and are at all impacted or concerned by these facts, explore how we treat security at Openprovider, or scan your website for free now.


